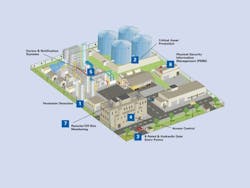
Over the past decade, chemical and petrochemical facilities have seen an increase in security-related regulations. The Maritime Transportation Security Act (MTSA), signed into law in 2002, had been under development prior to 9/11 but its initial focus on preventing crime, cargo theft and smuggling was expanded to address the threat of terrorism. Legislation mandating Chemical Facility Anti-Terrorism Standards (CFATS) to ensure the safety and security of chemical manufacturing, storage, usage and distribution channels was signed into law in 2007.
As a result of these regulations, chemical facilities are legally obligated to comply with specific security performance standards. MTSA is a broad-based regulation applying to various types of businesses, not just chemical ones, that operate on waterways. CFATS mandates security measures depending upon whether a site falls into one of four risk tiers that correlate with chemicals of interest (COI), standard threshold quantities and location.
Each facility poses unique challenges and risks. So, there's no one-size-fits-all security solution. That said, many companies with multiple facilities have introduced corporate security standards to streamline operations and ensure sites maintain expected security practices.
Fortunately, numerous advances in physical security technology have emerged and offer cost-effective options for chemical and petrochemical facilities; solutions formerly only available to the government and military are becoming more affordable for industrial use. These advances have brought significant savings, especially for perimeter security — enabling sites to rely less on security officers and cut operational expenses.
A security risk assessment is the first step to assessing a facility's needs and creating a sound yet cost-effective strategy factoring in both upfront and ongoing expenses (see sidebar at the end of this article). Risk assessment identifies security vulnerabilities and thus enables developing appropriate recommendations to secure a site and comply with applicable regulations.
PERIMETER SECURITY SOLUTIONS
For facilities covered by CFATS, perimeter protection and detection solutions specifically must help satisfy Risk-Based Performance Standards (RBPS) 1 —"Restrict Area Perimeter" and RBPS 4 — "Deter, Detect and Delay." Waterfront facilities regulated by MTSA face additional complications because perimeter security technologies must decipher between the constant movement of water and movements made by potential intruders. Advances in fiber-based technology, thermal imaging/infrared (IR), analytics software and remote video have created more robust and affordable solutions.
Fiber-based technology. This is one of several top perimeter-detection solutions. Available to commercial markets for the better part of a decade, fiber technology can be integrated into walls, rooftops, razor wire and, most importantly, fences — the true first line of physical defense. Some hardened fences now include prebuilt channels for fiber intrusion detection (Figure 1). These "smart perimeters" sense vibrations and attempted intrusion and also differentiate among environmental noise, wildlife and actual human activity. Fiber technology now can distinguish between types of human movement, such as cutting versus climbing. Several fiber-based detection systems are immune to the effects of radio transmissions and magnetic fields, can tolerate rapidly changing and unpredictable environmental conditions, and robustly resist wind and rain.
Recent advances in location-sensing technology have allowed these detection systems to pinpoint activity anywhere within 15 feet — a dramatic improvement from where the technology was just three to four years ago. Before location-based systems, fiber detection involved setting up zones ranging from one hundred to several thousand feet, which, if designed in conjunction with assessment cameras, created a delay in homing in on intruders. Location-based systems today substantially increase accuracy and prove extremely cost-effective because they eliminate the need for manual intervention to pinpoint an intrusion event.
In the past year, fiber-based fence technology has gained a redundancy feature — if an intruder were to cut through the fiber, the self-healing ring technology would remain fully operational. Today's "smart" fence, boasting redundancy and location-sensing technology, is in many cases the foundation for continuous perimeter protection.
Thermal imaging/infrared (IR). Once used almost exclusively by the government and military, thermal imaging solutions have become increasingly popular in recent years for commercial and industrial applications. In the past decade, the upfront cost of IR technology has decreased by two-thirds for some products, in part because of reduced amounts of germanium required in the lenses of thermal imaging cameras. As technology continues to evolve and the focal plane (the equivalent of a CCD imager in a normal camera) gets smaller, so does the lens, driving down the amount of germanium used and creating a more affordable and attractive solution.
Even in the most adverse conditions, thermal imaging can produce clear images based on heat radiation, which is almost impossible to mask (Figure 2). The technology consumes little power, works efficiently during both day and night, and only demands limited upkeep. This can translate into reduced maintenance and headcount costs.
Because they can cover more ground, thermal imaging cameras require less infrastructure investment than traditional surveillance cameras. They are easily mounted on poles, walls or other existing structures. They don't need perimeter lighting, which tends to be very expensive.
A large number of perimeter solutions installed within the last three to four years include thermal imaging. It's effective in areas with no other options and is especially useful for waterfront facilities where a light source typically is unavailable.
Analytics software. A conventional video surveillance system in many ways is the fundamental building block of any effective security system. Video is a strong deterrent to theft and fraud. Digital recording can document events and provide a level of organizational awareness and control that was unimaginable previously. The integration of video analytics software enhances security levels and capability. Layering analytics software onto video surveillance improves operations.
Analytics software can detect unauthorized intrusion and unusual behavior across a perimeter while eliminating external environmental factors. It filters data captured by video surveillance systems and can differentiate between emergencies and non-emergencies with more accuracy than human operators, who are prone to diminishing concentration levels and fatigue when continuously viewing video monitors. Coupling analytics software with video cameras helps rule out false positives from wildlife or other environmental factors.
Global-positioning-system capabilities can pinpoint the exact location of an incursion, enabling quick deployment of security personnel. Detecting human-shaped figures at greater distances allows more time for security to mobilize and provides a more-targeted search range. For CFATS compliance, the software can monitor restricted areas, deter internal theft and address vulnerability risks. Analytics software also helps lower overhead because it requires a minimum headcount to manage the system and cuts down on the need to review eventless footage.
Video analytics first became available in 2003; since then options have ballooned. Today, more than one hundred manufacturers offer video analytics. Two of the most important considerations in software selection are range and pixels-on-target. A greater range ultimately will be more cost-effective — by reducing the number of cameras and infrastructure needed. Pixels-on-target measures the accuracy with which a computer can detect an object — the greater number of pixels, the better the recognition.
Remote video. A managed video monitoring service, which various security providers now offer, can be a cost-effective solution for some companies, especially those with remote or smaller locations that don't have command-and-control stations or 24/7 guard shifts. Hosted video is specifically designed to reduce the amount of labor and technical know-how needed to provide video security at a site.
Such a system uses security professionals at an off-site central monitoring center to observe and record alarm-driven activities. These operators can confirm if alarms are real and not ones triggered by animals or other natural events — thereby reducing fines for false alarms. For real alarms, operators can follow the site's security protocol to notify facility personnel, law enforcement or other designated contacts.
The operators can visually tour facilities at specified pre-scheduled times. These tours are recorded with a date and time stamp along with appropriate notes and video clips to enable future recall. Using an Internet connection and Internet protocol cameras, end users also can access video remotely from virtually anywhere, anytime.
TYING SOLUTIONS TOGETHER
A layered approach to perimeter security can match the most appropriate technology to various points at each facility; most sites use four to six technologies (Figure 3). However, technology alone won't provide optimal security. It's essential for a facility to consider the people, processes and training necessary for a sound solution.
Another factor vital to site security is properly managing and processing information from the various technologies. This can be especially challenging when dealing with multiple technologies from various vendors.
Physical security information management (PSIM) systems make that job easier by centralizing command-and-control functions across virtually any combination of a facility's physical and logical security assets. A PSIM system offers a complete picture of all security activity in a single real-time view without the need to simultaneously monitor multiple consoles in the security center. It can help a company or site leverage existing investments in security technologies while enabling open integration with new technologies.
A PSIM system provides centralized views of security activities through a single graphical user interface. Using information from access control, video, intrusion and fire systems, PSIM allows security operators to better visualize incidents, assess situations and manage resources. The automated logical control can correlate events from those systems, bringing crucial alerts to the attention of security staff site-wide. It can enable security staff to observe alarm locations on a geospatial map and allows simultaneous viewing of live and recorded video. The system can be configured to manage and prioritize alerts based on templates and policies.
Alarm triggering can prompt automated incident-response workflows, ensuring a site's policies and procedures guide operator actions. This results in a more reliable and consistent security response and resolution that can be tracked and documented.
A PSIM system is useful in integrating technologies within a particular facility and across multiple facilities within a company to make certain each location complies with federal regulations and corporate standards.
Today more than ever before, cost-effective security technologies are available for industrial use. Ultimately, a site must choose the technologies that best suit its specific needs, comply with applicable federal and corporate regulations, and promote business goals.
DO THE ESSENTIAL PRELIMINARIES
The first step in creating a robust and integrated security solution is to evaluate your site's particular needs and risks. It's important to work with an integrator with full SAFETY Act certification from DHS (www.safetyact.gov/), as this level of know-how can help chemical facilities implement anti-terrorism technologies to protect people and property, while also providing important liability protections in the event of a qualified act of terrorism at the facility.
The assessment should involve:
1. Determining if any security regulations such as MTSA and CFATS affect your facility. In addition, a site covered by CFATS must understand the effect of its tier level: CFATS categorizes a high-risk site into one of four tiers — Tier 1 applies to facilities with the highest risk and requires the most stringent measures.
2. Understanding corporate security mandates and incorporating them into your overall strategy. Even if your company hasn't issued directives, it's a good idea to ask if standards or specific plans are in the works.
3. Including all critical assets in your plan. For example, control systems and COI can be considered assets but so can a section of a plant or even the entire plant itself.
4. Knowing your audience. The officials ultimately responsible for approving (or denying) a facility's security plan have not seen (and likely never will see) the site. In other words, the "boots on the ground" inspectors observe, report, assess and validate but don't make the actual approval/denial decision. Therefore, it's essential that a facility provides detailed descriptions, diagrams and photos to "paint a picture" of its security posture and environment.
More tips and information about complying with specific regulations are available at www.ADTbusiness.com/petrochem in downloadable chemical security whitepapers.
RYAN LOUGHIN is director of petrochemical & energy solutions for ADT Advanced Integration, Warwick, Pa. E-mail him at [email protected].