Chemical makers are increasingly focusing on protecting their process control systems from intrusion both from the inside and outside. Many manufacturers have made great strides in building this defense; a small percentage of top-tier enlightened control system suppliers and customers are applying best practices.
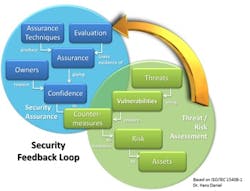
To get started addressing the security challenge, companies will benefit by implementing a security feedback loop as depicted in Figure 1. The process involves assessing threats to identify vulnerabilities and then providing appropriate counter-measures to minimize risk to assets. Its goal is to build consistency and confidence in how threats are addressed.
The loop represents an ongoing process. Security awareness and defense continue to evolve to meet the ever-changing threats and new vulnerabilities.
Security depends not only on such a process but also on attitude. You must assume the attacker is at least as intelligent and motivated as the defenders. While the weakest points in the system are the most likely targets, small actions and inactions may incrementally improve or compromise security. One of the most significant vulnerabilities is complacency; security demands ongoing vigilance.
TODAY'S TOOLS
Several aspects of security now are relatively robust, including:
Risk assessment. One of the logical first steps in determining the exposure of a control systems environment, it provides a summary of risk areas and actionable recommendations to either remove or neutralize the risk.
Policies and procedures. Rectifying issues found during the assessment may demand developing or enhancing policies and procedures governing the control system — many requiring that people within the organization have an awareness of security and best practices (i.e., a security mindset).
Segregated process and information technology. Security areas are defined and then segregated using firewall technology, including specialized firewalls for critical process control devices.
Locked down/least privileged approach. Interaction of personal computers with the control system defaults to an access level that avoids risks.
Dealing with "Denial of Service" attacks. This involves recognizing vulnerabilities and developing avoidance policies and procedures for squelching such attacks.
Virus protection. Providing an organized approach for verifying anti-virus software and definitions are up-to-date is essential.
Microsoft patches. Procedures must ensure the patch level is maintained and appropriate for the environment.
Backup/recovery. A company must understand its backup/restore requirements and develop procedures that make sure backups occur at appropriate times and are stored for later availability, and that the process for recovery is well-understood and communicated.
Security audit log monitoring. Capturing and reviewing network history can lead to insights about areas needing attention.
The understanding of these aspects varies among control systems personnel today; some have an in-depth program to address risks and vulnerabilities, while others are unaware of the risk and impact of an intrusion. The idea that control systems aren't vulnerable is eroding because we have recent history, such as the Stuxnet attack, that indicates vulnerabilities do exist (see: "Industry Gets Cyber-Security Reality Check"); the ill intentioned can exploit these vulnerabilities and uninformed internal sources inadvertently can trigger them.
Education of personnel is a key element in establishing an effective security strategy. Realizing that things such as unauthenticated connections between endpoints and cleartext communication can compromise current systems leads us to understand that this vulnerability enables the potential for a man-in-the-middle (MITM) attack, a form of active eavesdropping. Coupled with a lack of accountability — inadequate authentication and authorization to strongly enforce access — it's easier to make unauthorized changes to the configuration of systems.
WHERE DO WE GO FROM HERE?
Properly addressing the aspects cited above provides a foundation for effective security. However, as technology advancements are introduced into the control systems environment, the need for vigilance will increase, as will the importance of applying best practices and techniques. Fortunately, new technology and process evolution should help us make a step change in control system security.
Four techniques should play a significant role in improving security over the next five years: 1) whitelisting; 2) encryption; 3) incident detection and response; and 4) remote security operations centers.
Whitelisting. Perhaps you're familiar with use of the "white list" approach in e-mail management — specifically, for eliminating spam and allowing messages you want to receive. We see it today as a way to prohibit unapproved software/applications from running on the protected system. "Good" software makes its way onto the white list, while unauthorized software is kept from executing. Many enthusiasts believe whitelisting is a good safeguard against "zero day" intrusions (i.e., ones where defenders have no prior awareness of a vulnerability) — preventing some, but not all.
Whitelisting does put in place a capability to enable better change management, protecting against unauthorized alterations to the system configuration — an approach that might have provided some defense against Stuxnet. Some power companies now are implementing whitelisting as part of their critical infrastructure protection programs.
Forward-thinking whitelisting advocates are looking at advancements in the technology as a way to quarantine unauthorized software upon discovery, quarantine after blocking, enhance whitelist management, and produce a file system inventory that can accelerate verification of software on a hardware platform.
Whitelisting will be available for process control systems. Regardless of the depth of its initial usage, the technology will provide another layer of defense.
Encryption. A key issue today is that almost all communication on a control system is cleartext (a term sometimes used synonymously with plain text). This unencrypted text makes an MITM attack possible — allowing the intruder to "fake out" its victims, passing information as though it were a trusted endpoint, operating in a "trust the sender" scheme.
A solution is to encrypt communication. Encryption is the process of using an algorithm to transform text so "the message" is unreadable to anyone not possessing the encryption key. Encryption has a long history with the military and governments for secret communications. Today, we see it as a common method for protecting information in commercial systems and with wireless communication. One of the questions is where to encrypt the data — at rest or in transmission.
Encryption by itself can safeguard the confidentiality of messages, but protecting the integrity and authenticity of a message requires other techniques.
For process control, we recognize the need to defend against modification from sender and receiver endpoints. Today, with Internet Protocol security (IPsec), we can perform end-to-end authentication, protecting the message without encrypting the data. As an IPsec configuration option, data can be encrypted as well. However, encrypting data can cripple network intrusion detection capabilities. The security strategy for the control system environment must balance the benefits and select the appropriate set of options.
Incident detection and response. An intrusion detection system (IDS) is an application that can include both hardware appliances and software solutions. The IDS resides on the network and notifies the network administrator of intrusion attempts; it records all alert information according to parameters set by the administrator. Traditional information technology (IT) organizations have used these systems for many years, and we have found them equally useful in the control systems environment.
Some control systems today are integrated with network-based IDSs. However, over time we expect greater pervasiveness of this technology as well as the application of host-based IDSs.
An IDS can inspect network packets as they flow through the system. Today, however, IDSs understand very few control system protocols; we see that changing in the future as more of the protocols are defined and implemented, making IDSs more effective for control systems.
While detecting an intrusion is worthwhile, an even more attractive option is thwarting the intrusion. Intrusion prevention systems (IPSs) are relatively new but have a role to play in the future — by inspecting and validating communications attempting to pass between levels in the hierarchy, for instance, between business and process control networks.
Remote security operations centers. These help ensure optimal performance and administration of a process control network and security infrastructure via a set of remote services.
Many process control organizations today face challenges in addressing areas requiring specialized skills — ones that are more closely aligned with the IT organization. While these capabilities are both valuable and necessary, achieving business results commands higher priority for in-house resources. So, over the coming years, we expect growing use of this type of remote service to keep the process control network running in a secure environment.
SECURITY STRATEGY FOR TOMORROW'S PLANTS
Process plants of the future will be compliant with the IEC 62443 standard for industrial network and system security. This means IT best practices for security increasingly will be applied to process control.
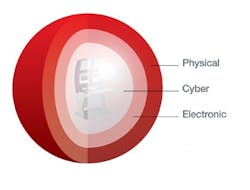
Plants will implement "defense in depth" — realizing a single "Maginot Line" won't suffice (see: "Protect Your Plant"). They will strive to safeguard control systems from physical, electronic and cyber attacks (Figure 2).
We will see a move toward more individual accountability — achieved through more role-based control and access-enforced endpoints instead of "in the middle" approaches. Today, change points are detected and made on the server. In the future, they will move nearer to where the impact of the change resides, in other words, closer to the controller.
For role-based access control, a way of increasing individual accountability, we will see encryption used as a step in the right direction. We must adopt a security mindset — based on the premise that all trust is limited. One element of that mindset is compartmentalization, to minimize what must be defended and potential loss.
We also must understand that unverified trust decays over time. So, we must re-verify the basis for trust, ensuring the verification testing isn't predictable. As part of our mindset, we must assume that "the attacker" has compromised some personnel and equipment, yet another reason why a single "Maginot Line" isn't enough.
As we move forward, we must recognize the management challenges involved in the security process. It requires never-ending effort, and involves more uncertainty than other business processes, with mostly indirect measures of success and potentially catastrophic demonstrations of failure.
Management must foster a culture in which security is every employee's personal responsibility. As with all continuing processes, people become complacent or develop workarounds without regard to consequences. So, ongoing use of the security feedback loop is crucial.
As we consider the next five years or so, we can see the "plant of the future" will take advantage of additional security technologies, more and more integrated into the control systems, with easy-to-use management and configuration tools. The security mindset will become ingrained in our control systems, just as safety has. Being prepared, informed and optimistic will help ensure continued success. Remember, it's an evolution — not a revolution.
JASON URSO is vice president and chief technology officer for Honeywell Process Solutions, Phoenix, Ariz. E-mail him at [email protected]