No trend in the past thirty years likely will revolutionize chemical processing as much as the imminent implementation of “digital transformation” technologies and practices. This transformation encompasses a proliferation of Industrial Internet of Things (IIoT) sensors and actuators, a flood of time-series data, and exponential growth in computers directly participating in plant operations. However, one central concept — low-cost implementation of change — will drive the real power and productivity benefits of digital transformation, namely, the ability to make rapid, iterative and data-driven innovations to plant operations at a fraction of the cost previously possible. This demands overcoming the restrictions to innovation created by closed proprietary systems.
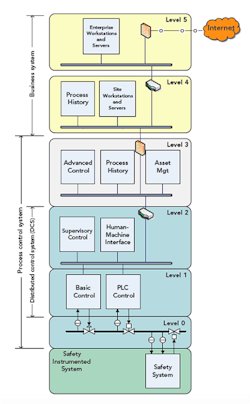
Figure 1. Manufacturers generally deploy process control and business system hardware in five levels.
Numerous factors are driving this need: global markets and competition make laggards in innovation unsustainable; changing environmental laws and sensitivities require new tools for compliance; and reimagined capital budgets consider operational flexibility and profitability not only efficiency and safety.
Digital transformation and asset performance maximization place a call on business systems, cloud and computing architectures, and process automation and control systems that operate manufacturing plants. Major global industrial and chemical companies are collaborating with leading process automation vendors and system integrators to accelerate this revolutionary change in automation through the adoption of The Open Group Open Process Automation Standard (O-PAS).
To fully benefit from the immense power of new digital tools such as artificial intelligence, machine learning, cloud computing, data analytics and edge computing, the chemical industry must adopt an open standard like O-PAS to accommodate and implement continuous change. Such a move will enable operating companies to affordably upgrade equipment in-situ, rapidly reconfigure production to respond to sudden market opportunities, and continually apply improved algorithms with deterministic results. Moreover, it will allow working within system constraints such as keeping human/machine interfaces and operational procedures usable by current and new workers, aggressively implementing digital security, and never compromising operational safety. O-PAS, the second version of which has just come out, provides a critical standards framework to address all these factors and many more.
The Current Situation
Since the 1970s, the state-of-the-art for process control and business information systems at process plants has consisted of a multiple-level hierarchy of interconnected computing devices, sometimes called the Purdue Model. This hierarchy (Figure 1) has the process control systems as Levels 1 to 3 and the business systems as Level 4 and 5.
The process control systems, usually described as distributed control systems (DCSs), monitor and control manufacturing processes. A DCS typically consists of operator and engineering stations, controllers , input/output (I/O) modules and application servers. Such control systems generally remain in service for a long time, often for decades, even as the surrounding business network and enterprise systems (Levels 4 and 5 in Figure 1) are upgraded. The closed proprietary nature of Level 1–3 systems provides a significant obstacle to change at those levels.
However, for legacy systems installed in the 1980s and 1990s, obsolescence of components is a real problem. Obtaining hardware and patching the software to keep the systems running are increasingly difficult; loss of institutional memory and programming skills for legacy systems compound the problem. Opting to “rip and replace” the installed system is very expensive and time consuming, affecting both productivity and profitability. Moreover, closed systems don’t allow for ease of access to data that complex algorithms use to generate actionable operational insights that can boost productivity and truly drive a digital-enabled organization. The concept of a layered hierarchy of access seems increasingly at odds with the emerging trend of open access to data and trends in digital enablement.
Security was an afterthought in legacy systems; the majority of security measures focused on physical access controls. As networking and computing technology improved, strong business drivers emerged for interconnecting these networks to allow centralized process control and sharing of information across the enterprise. The convergence of once-isolated control systems with information technology (IT) networks has introduced new security risks, exacerbated by lack of encryption and authentication technologies as well as availability of open-source information regarding industrial control system architectures, operations and vulnerabilities.
In addition to the technical issues, legacy systems pose an inherent business problem by strongly favoring incumbent suppliers. The closed proprietary nature of the interfaces enables those vendors to control access and affords them “vendor lock,” whereby they gain a recurring revenue stream for provision of exclusive services.
An Alternative Model
Given the limitations of the current approach to process control, what should an alternative model encompass? It should contain four major elements that can provide a framework for creating an improved automation system.
1. A distributed, modular, extensible and scalable platform that lowers the cost, complexity and operational risk associated with expansion or online replacement (to deal with component obsolescence or to open up new opportunities), and that exploits the increased computational power in endpoint (edge) devices to improve application capability and effectiveness. In this new platform, the applications could access data at any of the control nodes as needed, unlike the traditional model.
2. Standards-based open interoperable architecture that offers the freedom to choose any procurement strategy, allows owners to preserve custom software for the lifetime of the plant asset, provides incentives for software developers to create and sell directly to asset owners, and enables integrators to connect different hardware and software components without modification.
3. Designed-in security using a standards-based secure architecture that allows asset owners to protect against known risks, detect abnormal situations and evolve with emerging threats.
4. A less-complex and more-productive user environment realized via technologies such as plug-and-play field devices, flexible notification capability and an enterprise-wide asset information portal. These would enable workforce empowerment and innovation through use of industry standard tools for creating applications.
Figure 2 shows a reference architecture to illustrate what the future might look like.
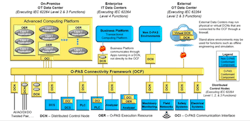
Figure 2. Unlike current proprietary control systems, an open one based on O-PAS readily integrates multiple vendors and enables easy upgrades.
The Open Process Automation Reference Architecture flattens the design, eliminating the hierarchical nature, and attempts to ensure data are always available to the desired user with the minimum overhead. An important aspect of the new architecture is the concept of a distributed control node (DCN) as the edge device connected to the field wiring. Many functions of today’s DCS and programmable logic controller (PLC) systems might migrate to the DCN. The DCN will include I/O signal processing as a minimum, with the potential to have expandable computing capability. Depending on the functional requirements, the DCN could host regulatory controls, more-advanced control applications and, eventually, advanced optimization and analytics applications. The future world includes the capability to run the latest applications directly at the edge, if required for data latency or availability. This allows for future-proofing as new possibilities open up on how plants are operated and monitored.
A real-time bus provides the data backbone to connect the DCN and all components in the system. For brownfield applications, gateway devices would allow integration of legacy devices into the new architecture. A high-availability advanced computing platform supports the system and provides the computing power to host applications that don’t need to run at the edge. Examples include abnormal event detection, procedural automation, advanced control and process optimization. In the new architecture, data are readable from the source in the DCN to either a local enterprise-level IT data center or to external data centers with proper security authentication and based on trust as defined in the standards-based security protocols. This allows for true business control of operations and, thus, fosters the success of digital initiatives.
The Role Of OPAF
The Open Group Open Process Automation Forum (OPAF), www.opengroup.org/forum/open-process-automation-forum, has a broad scope, encompassing today’s DCSs and PLCs for the continuous and hybrid process industries. Its core work is to define the standards for an open, interoperable, secure process automation architecture. The Forum is using a “standard of standards” approach to minimize re-work and avoid “reinventing the wheel.” The Forum will select the best available standard from existing applicable industry standards. When no applicable standard exists, the Forum will work with standards-development organizations to generate a standard. The ultimate goal is to create a thriving marketplace of software and hardware components that use standards-based open interfaces to allow for easy integration, interoperability and more innovation.
Open automation does not require open sourcing. The published standard provides public exposure of software and hardware interfaces and data definitions but a supplier need not reveal the inner workings of its hardware or software component nor does an end-user divulge applications it has developed.
Joint workshops held between end-users and suppliers led to development of a set of quality attributes (QAs) — nonfunctional system characteristics that influence system quality and drive architectural decisions. These QAs serve as touchstones in guiding the work of the Forum. A few key QAs are: interoperability, modularity, interchangeability, conformance, securability and portability. The Forum considers the QAs of safety, resilience and maintainability as fundamental to any O-PAS product, so these aren’t called out separately.
A Key Difference
Unlike other standard-development activities, the Forum isn’t just a technical effort. In addition to a technology working group (TWG), the forum has created a business working group (BWG) to establish viable business practices and procedures to conduct business in the new open environment. The BWG’s role includes reducing impediments to commercial success and providing guidance to the TWG. It has published “The Open Process Automation Business Guide,” https://publications.opengroup.org/g182, that defines the ecosystem roles in the new business environment and offers a roadmap for suppliers, end-users, service providers and system integrators about the value proposition and benefits to the participants.
An important part of the task of the Forum’s Certification Work Group is to develop a policy for conformance and certification and to maintain a registry of conformant products. For a component to be registered and discoverable, it must conform 100% to the published standard. Outside accreditation laboratories, selected by The Open Group Certification Authority based on the standard, will verify conformance.
The TWG is charged with developing the standards. Specialist subcommittees handle security, interoperability, technical architecture and portability, among other components. In addition, an enterprise architecture working group manages the use-cases and translates the business guidance into technical requirements to guide development of standards. The Forum has partnered with a variety of industry associations and standard-development organizations such as the International Society for Automation (ISA), OPC Foundation, NAMUR, CSIA, FieldComm group, PLC Open and others consistent with the “standard of standards” approach.
The New Ecosystem
In the traditional model of automation procurement, the DCS vendor configures its available offering of proprietary hardware and software components to meet end-user specifications. The resulting package reflects the special relationships between the vendor and component suppliers, with integration issues handled by the DCS vendor using proprietary interfaces.
By contrast, in the new ecosystem model, a systems integrator (SI) assembles a system to meet end-user specifications using cost- or performance-advantaged O-PAS-certified hardware and software components. This should ease integration and reduce development cost because there’s a loose coupling that enables the different components to work together, facilitated by certified and standards-based interfaces that allow for stitching together the system quickly and efficiently.
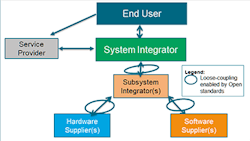
Standardization of interfaces lowers the barrier to entry. Therefore, additional specialist hardware or software suppliers can compete, allowing for more innovation. The new ecosystem explodes the monolithic role of the DCS vendor into different constituent roles such as systems (and subsystem) integrator, hardware and software suppliers, and service provider (Figure 3). It’s important to note that the new ecosystem model is a role-based model. So, a supplier may serve as a SI or service provider for a given project. It also allows for more players to enter and perform the role of an integrator, increasing competition. Accountability for system performance rests with the systems integrator or SI, as spelled out in Section 4.1 of the Business Guide.
Figure 3. Exploded view shows interconnections between roles of end-user, systems integrators, hardware, software suppliers, subsystems integrators and service provider.
Broad Guidelines
The Forum is advancing an entire supplier/buyer ecosystem of traditional DCS vendors, SIs, digital technology providers and process manufacturers toward an open business model. Consequently, the OPAF also establishes business practices for how this open marketplace should operate, unlike traditional technology standards from groups like ASTM International or the Institute of Electrical and Electronics Engineers.
Operating companies implementing systems containing O-PAS-certified components benefit from the capability for continuous process improvement through rapid application of the latest available hardware and software. Once adopted, software applications and system configurations are portable and reusable across systems, reducing total cost of ownership. In addition, end-users gain access to a more-competitive market of offerings and minimize customized development associated with proprietary components. Solution providers also benefit from access to new market opportunities, continued relevance to existing and prospective customers, and reduced development costs due to the entry of smaller specialized suppliers that add value and innovation.
Through the Forum, each incremental definition of the O-PAS technology is matched by business guidelines for use-cases, industry involvement and detailed certification procedures for conformance. Forum members are working to provide the vision, understanding and framework for end users to make intelligent and strategic decisions about future plant operations and designs. The entire process automation ecosystem is moving forward together.
For example, these changes in ecosystem allow for new business models to evolve similar to the changes in the enterprise IT business (e.g., software as a service) and transference of owner-controlled operation to a “tolling” model reflecting the desired level of owner involvement.
Technical Components
The O-PAS Standard includes eight parts:
• Part 1 — Technical Architecture;
• Part 2 — Security Aspects;
• Part 3 — Profiles;
• Part 4 — Connectivity Framework;
• Part 5 — System Management;
• Part 6 — Configuration Portability;
• Part 7 — Physical Platform; and
• Part 8 — Application Portability.
Here, let’s take a high-level look at three wide interest aspects: cybersecurity, communications and system management.
Cybersecurity is an O-PAS imperative and of upmost importance to OPAF members. Managing security (Part 2) in a highly distributed environment such as in O-PAS requires consideration of security in all elements of the technical architecture (https://publications.opengroup.org/s184), including the physical and communications platform, operating system, system management services and applications. The security specification is based on the broadly accepted ISA/IEC 62443 Security for Industrial Automation and Control System standards. An O-PAS environment may consist of thousands of O-PAS-conformant components from multiple vendors. Version 1 focuses on providing O-PAS-conformant components from a product supplier that can be made secure in a system configuration (see: “O-PAS Version 1 Explained,” https://bit.ly/2YBPt3V).
The Connectivity Framework (Part 4) defines the information models and transport protocols for communicating data using Open Platform Communications Unified Architecture (OPC UA). Version 1 describes the necessary OPC UA security and services to ensure interoperability for OPC UA clients and servers and the services for client/server actions and for publish/subscribe communication. The “Version 2 Preliminary Standard,” https://publications.opengroup.org/p201, which came out in late January, adds standard information models for DCNs, signals, alarms and function block applications.
System Management (Part 5) uses the Distributed Management Task Force Redfish standard. Version 1 focuses on providing system management of compute node hardware (e.g., chassis, board, and cooling information for hardware with and without a baseboard management controller). Version 2 extends system management by operations-technology-specific DCN information including runtime, metrics and sensor interfaces, as well as in-band operating systems information and metrics.
Version 2 of the standard (https://publications.opengroup.org/i201m), which was published in January 2020, addresses portability of configurations. Version 2.1, scheduled for publication in the second half of 2020, extends definitions for information exchange models and standard interfaces that support some event processing, and standards-based application processes. Version 3 will focus on application portability.
Current Status
Since its inception in January of 2017, the OPAF has grown to include more than 90 companies from around the world. Each iteration of the standard will undergo testing in real-world scenarios both to guide development of the O-PAS as well as to demonstrate feasibility and viability. Because “seeing is believing,” OPAF held its first interoperability workshop in June 2019 based on Version 1 of the standard. The second workshop is planned for the third quarter of this year (but may be delayed depending upon Covid-19 travel restrictions). Companies evaluating design and purchasing decisions should review “O-PAS Certification Policy,” https://publications.opengroup.org/x201, which was published in February.
Separately, some member companies have developed an active “test bed” to prove out and refine O-PAS-compliant technologies from multiple vendors.
Key success factors for the activity are a critical mass of input from end users and consensus among members in the ecosystem. The adoption and success of O-PAS standard will significantly impact automation and process control in the continuous and hybrid process industries by expanding innovation while improving security, flexibility and productivity — maximizing asset performance. Don’t let your company be left behind.
MOHAN KALYANARAMAN is technology acquisition advisor, strategic planning for ExxonMobil Research and Engineering, Annandale, N.J. DON BARTUSIAK is chief engineer, process control for ExxonMobil Research and Engineering, Spring, Texas. STEVE BITAR is R&D program manager for ExxonMobil Research and Engineering, Spring, Texas. BRADLEY G. HOUK is senior engineering advisor for ExxonMobil Research and Engineering, Spring, Texas. DAVID L. DEBARI is instrument engineering associate for ExxonMobil Research and Engineering, Spring, Texas. BRANDON WILLIAMS is executive vice president of CPLANE.ai, San Carlos, Calif. Email them at [email protected], [email protected], [email protected], [email protected], [email protected] and [email protected].