When surveyed at the Black Hat USA 2017 information security event in July in Las Vegas, 60% of attendees said they believe a successful cyber attack on U.S. critical infrastructure will occur in the next two years. More than two-thirds reckon their own organizations will have to respond to a major security breach in the next 12 months.
Chemical companies, understandably, don’t want to reveal the cyber-security steps they are taking. For instance, Dow Chemical, Midland, Mich., and Eli Lilly, Indianapolis, Ind., wouldn’t comment for this story. Lubrizol, Wickliffe, Ohio, did say that it totally prohibits the use of USB flash drives on its control systems. Lanxess, Pittsburgh, Pa., ensures the safety of employees, customers and local communities with a wide array of site security measures, in compliance with Department of Homeland Security requirements, notes president and CEO Antonis Papadourakis.
[callToAction ]
Cyber-security breaches often result not from remote attacks but instead from local actions such as staff or contractors using infected USB flash drives and laptops or from physical incursions, experts note. Fortunately, rapid advances in technology — from malware detection and remediation to perimeter protection — are giving plants better tools to address these threats.
The infected USB flash drive remains an ongoing threat for introducing malware, mostly as a result of activities by unknowing, untrained or unconcerned employees or contractors, stresses Galina Antova, co-founder and chief business development officer of Claroty, New York City. So, ongoing training and awareness campaigns still are important, bolstered by technology controlling the use of USB ports on the plant floor.
Figure 1. To be usable, USB flash drives must undergo checking by device at site. Source: Honeywell Process Solutions.
“While the USB threat remains an issue, it is diminished, in relative terms, to the risk of the extended attack surface that has resulted from the rapid convergence between business and industrial networks. Third parties such as contractors and industrial control system (ICS) equipment vendors — together with employees not located at the plant or working from home remotely — connect to the plant network via a VPN [virtual private network] that typically terminates to a ‘jump box.’ From there, the employees or contractors have unfettered access to any of the equipment in the environment,” she explains.
Following extensive consultations with customers, including chemical companies, Claroty has developed Secure Remote Access (SRA) to tackle this. It works by dictating which assets employees or third parties can access or see. It also enforces company authentication policies.
The remote access session is recorded for auditability. Also, importantly, an administrator, such as a security team member, network manager or plant engineer, can watch exactly what is being done — getting a virtual “over the shoulder” view of the session.
“In addition to auditability for security and compliance purposes, the session view and recording helps prevent a big issue that asset owners have with third parties saying they will be doing certain changes and then making other changes that were not previously authorized and possibly endangering process reliability, safety and security,” adds Antova.
This approach boasts two key differentiators, she says. First, it leverages the company’s background in and deep understanding of ICS protocols and the hazards posed to chemical companies by poorly designed information technology (IT) centric technologies. Second, SRA is integrated into Claroty’s Continuous Threat Detection product — giving security and plant floor teams a consolidated picture of potential risks.
“With Continuous Threat Detection, chemical customers have often identified multiple network configuration (network security hygiene) issues and were able to fix them before they served as an attack vector. The chemical teams also commented that the ability to control and monitor third parties has helped improve security and resolved the issue with third parties going ‘off script’ when making remote changes to the environment without being monitored or reviewed,” she notes.
Ratcheting Up Response
Achieving a cohesive security strategy requires investing in threat detection, remediation and response, counsels Moreno Carullo, CTO of Nozomi Networks, San Francisco.
“As threats evolve, and as OT [operational technology] converges with IT environments, we see a greater emphasis being placed on identifying and reacting to cyber threats, rather than simply trying to prevent cyber threats altogether. Preventative solutions and technologies need only to fail once, while reactive and remediation solutions are able to mitigate cyber threats, learn from and advance against them,” he says.
The company’s SCADAguardian tool uses artificial intelligence (AI) and machine learning to develop a comprehensive model of a network, its devices, connections and operational baselines. It uses this same technology to continuously advance its anomaly detection capabilities and analytics engine.
Carullo cites the case of the Industroyer virus, which is considered to be the biggest threat to industrial control systems since Stuxnet.
Here, SCADAguardian identifies process anomalies during phase one and phase two of an attack. Phase one, the infection phase, is when the malware establishes itself on a network and uses backdoors such as USB flash drives or contractor laptops to reach an external command and control (C&C) server. Phase two is when the C&C server directly pings nodes within the network to develop detailed understanding of devices and network operations in a chemical processing facility.
“In real time, SCADAguardian uncovers anomalous process behavior, a change in network traffic and any changes in process control such as irregular switch or PLC [programmable logic controller] demands. So any anomalies are isolated and remediation actions taken before system interruption. In addition, proactive threat-hunting capabilities include rules-based analysis and the use of signature assertions,” explains Carullo.
Nozomi intends to further improve the accuracy and speed of its threat identification and remediation capabilities. Carullo also envisions advances in SCADAguardian’s integration platform to more easily scale with enterprise environments, applications and operating systems.
Uncovering USB Threats
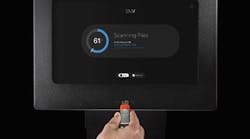
Secure Media Exchange (SMX) from Honeywell Process Solutions (HPS), Houston, is aimed at USB-borne threats and was designed based on feedback from chemical and other process customers and cyber-security experts.
“The bottom line was the need for a product that provides maximum security but doesn’t interfere with the normal business and operations of a process control facility,” says Phoenix, Ariz.-based Seth Carpenter, lead cyber-security technologist, strategic innovation group.
As a result, a plug-and-play cellular option was introduced that doesn’t connect to the plant’s network at all but rather to HPS’s secure cloud service ATIX.
“Through ATIX, we monitor and manage the SMX gateways as well, so the customer never has to spend any time maintaining SMX,” notes Carpenter.
ATIX is one of the three key components of the SMX product. Second are the SMX intelligence gateways, the physical units installed at a customer site (Figure 1). Anyone wanting to use a USB removable storage device in a protected personal computer (PC) must connect it to one of these gateways before it’s allowed on to a protected system. The final component is SMX Endpoint Protection Software installed on each PC protected by SMX. It ensures that any USB removable storage device has gone through an SMX Intelligence Gateway before use on the PC. If someone forgets to use the gateway first or the protection on the drive is tampered with between the gateway and the protected computer, the protection software will block the use of that drive.
“So, there is a central gateway (or set of gateways) that performs the analysis and verification of all USB drives. All drives must be brought to one of these gateways before use on a protected PC. There is also software which runs on each protected PC to ensure that users cannot skip the analysis and verification steps. It also gives us the granular control to quarantine and disallow individual malicious files but still allow other approved files to be used as needed,” he stresses.
Figure 2. Monitoring picks up person that has gotten by fence at site. Source: PureTech Systems.
In addition, by leveraging ATIX, SMX analysis in most circumstances is faster than a local anti-virus scan. HPS in the coming months expects to introduce further tools to streamline this process, he adds.
As part of its constant evaluation of new threats, the company is very interested in running potentially malicious software in a sandbox specifically tailored to a control system environment.
“Some advanced malware may try to avoid detection by remaining dormant until it detects that it has spread to its target environment. These tailored sandboxes may allow us to catch malicious behavior that would go undetected by traditional mechanisms,” Carpenter explains.
Policing The Perimeter
Because intruders can engage in cyber as well as physical attacks at facilities, operating companies are hardening their perimeter defenses, too. PureTech Systems, Phoenix, which specializes in developing video analytics surveillance software, counts a raft of chemical companies including ExxonMobil, BP Global, Honeywell Performance Materials and Chemicals, Occidental Chemical and Shell as customers. It also provides physical security for the protection of chemicals and fuels during shipping and storage.
“Chemical plants primarily have three main security concerns: protection of property, protection of lives and how to achieve this on a limited budget,” notes vice president of marketing Eric Olson.
They also face the extra concern that inadequate protection of their assets can cause detrimental effects well beyond their fence lines, impacting people and property nearby, he adds.
Olson’s major challenge concerning perimeter security at chemical plants is getting companies to accept a true return on investment (ROI): “Security spending is a very tough value proposition. Yes, you can consider its ability to reduce vandalism and theft, but it’s difficult to leverage its value against lives saved, either at the facility or the neighboring population. It’s unlikely the CEO is lying awake at night worried about the security of the facility, and the odds of a terrorist-type event occurring to any particular location is statistically very low.”
Hence, companies usually set a low budget for perimeter protection and don’t update systems in place in a timely manner, leaving chemical plants an easy target for intrusion, laments Olson.
A catastrophic event and government/industry mandates are the only mechanisms that seem to tip the ROI scale in these situations, he adds.
PureTech’s involvement with the chemical industry focuses mainly on safeguarding the storage or transfer of harmful and potentially harmful substances. This may involve monitoring for a direct intrusion (Figure 2) or for a series of indirect activities such as loitering around perimeters or critical assets.
“Plants typically have fairly large perimeters and video analytics can utilize commercial off-the-shelf security cameras to provide intelligent surveillance over long distances, up to several kilometers. That protection is more than just surveillance: it includes intelligence, meaning knowing the difference between a passer-by and a person loitering; the ability to track a suspicious target automatically with a camera; and assessing a target’s level of threat based on attributes such as speed, location, intruder type, etc.,” explains Olson.
Because intelligent video technology underpins a broad range of emerging applications including driverless cars, it will become more affordable, use ever more powerful algorithms and get combined with deep learning technology, he forecasts. “It will recognize more involved issues and patterns that may suggest foul play. It will also bring more automation to the process, meaning more surveillance and increased security response without the need for an increased security force to manage it.”
The company itself is advancing the technology. PureTech in June received a patent on a video-based detection and tracking system that uses the company’s geospatial video analytics technology to track aerial targets such as drones and aircraft. (For more on efforts to reduce risks posed by drones, see: “Washington Targets Drones.”)
Its current PureActiv system can use drones positively — as a means of adding airborne surveillance and response to a facility’s surveillance arsenal. Features such as drone-dispatch-to-event integrate drones into existing video surveillance systems to provide extended video protection.
Fully Automated Drones
The need for a pilot on the ground to control a drone imposes some limitations, such as in range. However, changes are more than in the wings. Indeed, Airobotics, Peta Tikva, Israel, has just gotten the world’s first approval to fly fully automated commercial drones without a pilot. In essence, the company’s software and AI replace the pilot.
The Civil Aviation Authority of Israel (CAAI) granted certification following two years and over 10,000 flight hours of extensive testing and trials, largely at Israel Chemicals and Intel sites in the country.
Airobotics sees the security potential of such drones for perimeter patrol routine surveillance, risk tracking and monitoring, threat assessment and defense against intruders.
The company has started its first commercial operation in Australia — for a mining company — and now is looking to the U.S. for further expansion.